It seems that having a perfectly secured web application guarantees no unauthorized access to your sensitive data. But what if instead of trying to hack the software, the attacker exploited your natural inclination to trust? Social engineering is the art of manipulating people so they give up confidential information. There are various kinds of desirable data, such as usernames, passwords and card details on top, which attackers can later use to steal your identity and money. Criminals use social engineering tactics because it is usually easier to trick a person to reveal their password than to break into a system unless the password meets complexity standards.
Assuming that humans are still the weakest link in the cybersecurity field, we should try to raise our co-workers’ awareness of the risk, and propagate the knowledge about how to defend against social engineering attacks.
Phishing
Phishing is an attempt to obtain sensitive information by disguising oneself as a trustworthy entity. Although the ultimate goal of phishing is always the same, there are many ways to perform this type of attack. Here are just four of them:
- Email phishing — using email messages to pretend to be a legitimate organization or person that attempts to fraudulently obtain private information
- Vishing — also known as voice phishing, is the criminal practice of using the telephone system to convince a victim to provide access to personal or financial information
- Smishing — this vector uses SMS text messages to convince the victim to take an action that compromises their information or device
- Impersonation — the attacker pretends to be someone else with the goal of gaining physical access to a target location or system
Recognize a phishing scam
As phishing scams imitate reliable entities, it is crucial to learn how to distinguish between real and fraudulent messages and websites. There are some basic rules to follow to help you detect a scam.
Verify the email address

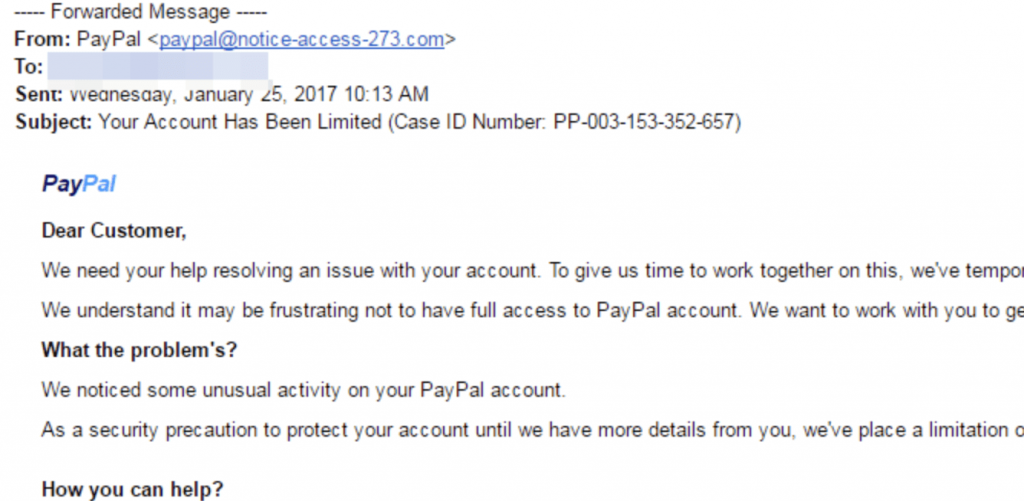
Users often look exclusively at the sender’s name displayed in their inbox, seeing a text like “PayPal” and the subject line. When recipients open the message, they already think they know who the message is from and focus only on the content. It’s always better to carefully investigate the whole email address before reading the message — don’t only pay attention to the sender’s name but also examine the exact email address because attackers can easily spoof it. Below you can see an example of email spoofing.
Source: https://www.itgovernance.co.uk/blog/5-ways-to-detect-a-phishing-email
On the surface, this may seem to be a genuine email from PayPal but after a quick analysis we can spot a strange domain in the sender’s full email address. Instead of an original PayPal domain, there is a “[email protected]” address.
Read the email thoroughly
First and foremost, let’s focus on the email’s purpose. The most common scam messages involve one of the following topics:
- Threat — the attacker informs you that some problems will occur unless you follow the instructions or that something bad has already happened and you have to act quickly to solve the problem. Common examples include a blocked account, a hack, or some other panic-inducing situation.
- Urgency — email content is urgent and persuades you to act immediately. For instance, the hacker explains to you the need to make an immediate bank transfer on your supervisor’s request or to update your password in order to avoid the expiration of an important account.
- Unusual opportunity — the attacker makes you think that there is a special chance to gain a financial benefit. This may concern a large amount of money you just have won although you never participated in any lottery, an inheritance from a relative you have never heard of, or some attractive discounts on the products you are going to purchase.
The next thing worth paying attention to language use and correctness. Spelling and punctuation mistakes can indicate a scam because the language used is often not the attackers’ native tongue. However, while crafting the email content, the scammers can be supported by a spelling checker or translator which considerably decreases the risk of overlooking typos. That is why it is advisable to look for grammatical errors which are usually harder to avoid.
Lastly, remember that established brands do not require giving up any confidential information via email. If you see a message with a valid company logo and address which asks you to click on a link to enter your sensitive data, this is almost certainly a phishing attempt.
Examine links before clicking on them
All links included in emails, or any other type of text messages, require special attention and should be always treated as potentially harmful. They may lead to fake websites that try to steal passwords or credit card numbers even though on the surface, they look completely legitimate. An attacker can hide the real destination address of a link in a text, button or image so at first glance, it is not obvious where the link leads.

Source: https://www.malware-traffic-analysis.net/2018/04/20/index.html
In the example above, you would expect that clicking the “Validate your membership now” button will redirect you to the Spotify website. Unfortunately, the link leads to a fake destination address marked in red in the screenshot.
To avoid opening a fraudulent web page, you need to check where URLs target before opening them. This only takes a few seconds and might be the best and the easiest phishing prevention: hover your cursor over the link — the real address will appear in a small bar along the bottom of the browser. On mobile devices, you need to hold down on the link to display a pop-up containing the URL.
Beware of attachments
Apart from the links, a phishing attack can involve email attachments. An infected attachment is a file containing malware which the victim activates on their computer either by downloading or simply opening it.
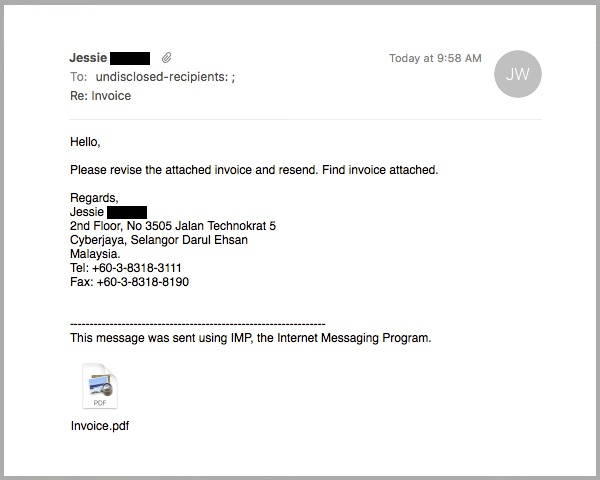
One of the most common examples is a fake invoice, like the one below:
Source: https://www.mailguard.com.au/blog/fraudulent-invoice-email-carries-an-adobe-id-phishing-pdf-attachment
Most often, the recipient will have to open the invoice to see what it’s for. In such a case, the attacker does not even have to do any research on potential expenditures of their victim beforehand. They usually try to simulate some urgent charge, like an important document from the boss or a service provider.
First of all, it’s not advisable to open any attachment unless you’re fully confident that the message is from a legitimate source. But even if you do recognize the sender, it is always safer if you’re expecting the attachment. For example, when the service provider notifies you of the charge first.
Take a closer look at the page you open
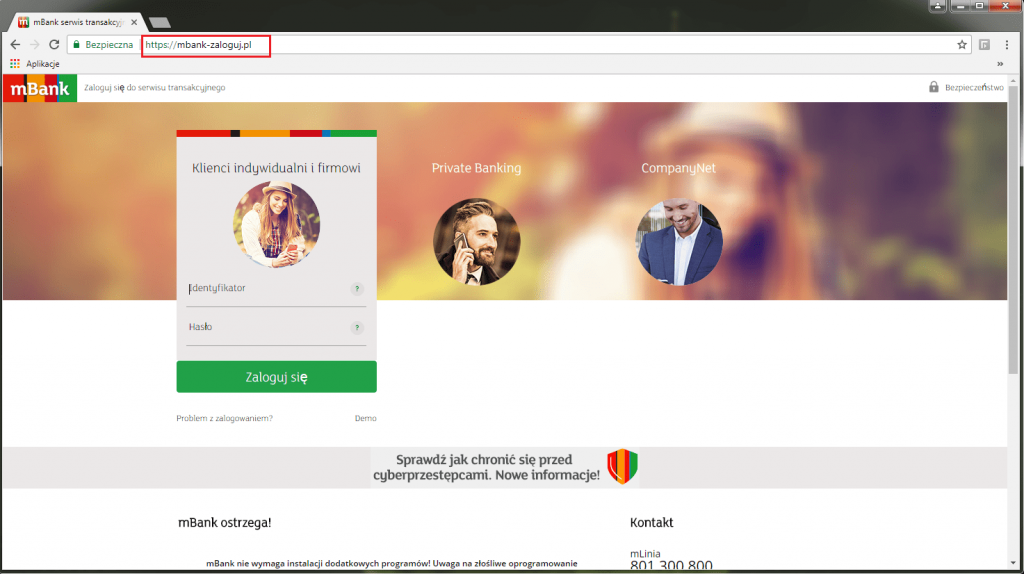
You can improve safety not only by avoiding opening malicious links and attachments but also by analyzing the page you have already visited to make sure that it is not fake. The first thing that should draw your attention is the URL address bar. The difference between a legitimate and fraudulent address may be subtle as in the screenshot below.
Source: https://www.mbank.pl/informacje-dla-klienta/post,7914,falszywa-strona-mbanku.html
As a whole, the mBank login page looks deceptively similar to its legitimate counterpart except the URL which has a clearly different wording compared to the original address:
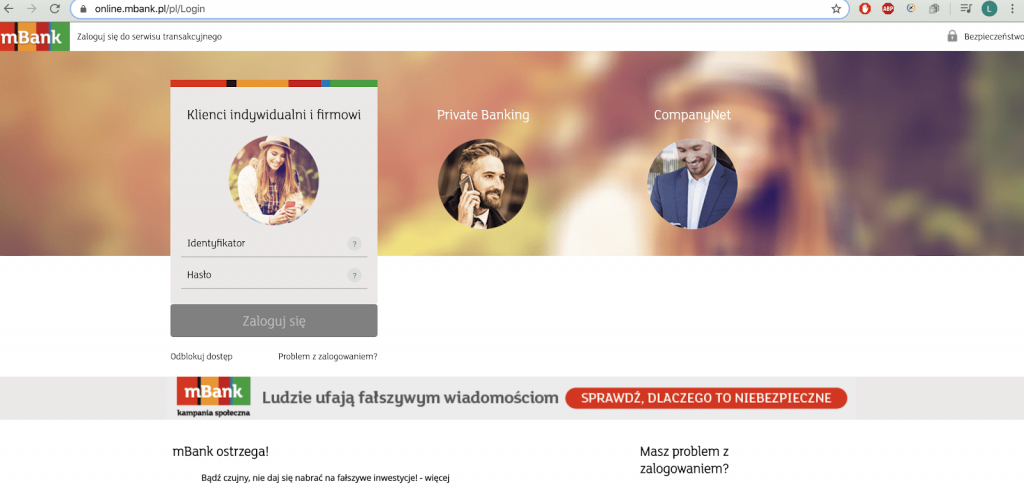
Source: online.mbank.pl/pl/Login vs mbank-zaloguj.pl
The difference may concern not only wording but also the replacement of particular letters, doubling or omitting them.
| Real address | Fake address |
| www.github.com | www.glthub.com |
| www.amazon.com | www.amozon.com |
| www.google.com | www.gooogle.com |
| www.victoriassecret.com | www.victoriasecret.com |
| www.homedepot.com | www.homdepot.com |
| www.microsoft.com | www.rnicrosoft.com |
Furthermore, a homograph attack allows to replace the letters with the characters that look exactly the same.
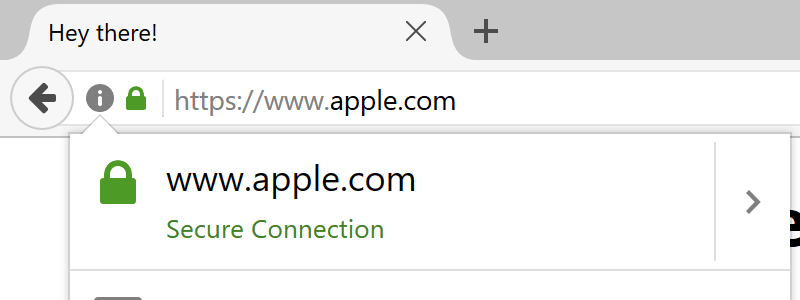
Source: https://www.xudongz.com/blog/2017/idn-phishing/
The above Apple web page is obviously not real. The homograph attack technique with the www.apple.com proof of concept is thoroughly described here.
Besides verifying the address, it is widely believed that the green padlock you can see next to the URL guarantees that the website is secure. In fact, the only thing you can be sure of while seeing such an icon is that the traffic to and from the website your browser is connected to is encrypted — this means that phishing sites can show the green padlock as well.
To recognize a fake website, it is better to check if its certificate is valid and comes from a trusted source.
Protect yourself from phishing scams
Phishing scams continue to escalate at alarming rates — every single day cybercriminals come up with more and more sophisticated social engineering techniques. That is why phishing scams are still a commonly used and successful fraud method. Nevertheless, the more aware of the risk you are, the less probably you will become a victim.
To sum up, let’s gather the safety measures that can be taken against phishing scams:
- Slow down. Scammers want you to act first and think later. Read all the messages thoroughly, try to search for potential danger before taking any action. If you realize a sense of urgency or high-pressure sales tactics be skeptical — do not let the urgency influence your careful review.
- Do not open all links you get. Control the website you land at by typing the destination address in the URL bar. However, if you need to click on a link, hover over it and check the real address beforehand.
- Watch out for attached files. Unless the sender is somebody you know personally and you expect a file from them, downloading anything is a mistake.
Do not trust every website you visit. When you open a web page, look around before entering any sensitive information. Make sure that the URL address is the one you expect to see and check the certificate.
For more tips on security and ways to design systems to protect your own users, drop us a line!
See also:
- To avert a service outage crisis — prepare, prepare, prepare
- Good reasons not to skimp on QA testing
- Outsourcing your online payment gateway project: What skills to look out for when building your remote team
- Unit tests and why not to skip them in your app development project
- How to build a secure and customer-friendly online payment solution




